Phishing Tactics for Red Teamers Part 1
Introduction
The goal of this series of blog posts is to give insight into one of the most prevalent tactics threat actors and cyber-criminals use to obtain initial access to an organization. Hence a deeper look into the more “fun” side of phishing tactics than your ordinary password-protected zip or credential harvester.

In my role as an analyst, a big part of my job is to identify and keep track of the latest threat actor behavior in order to be able to keep systems and people safe. Due to Microsoft’s recent changes to how macros work in office applications, I believe threat actors will adapt and shift towards new tactics.
Reference:

In this blog post, I will go through a tactic known as “Calendar Spoofing”; I will not just display how the phishing attack is carried out but also discuss how defenders could hunt for these types of initial access attempts.
Attack Methodology
The core of the attack relies on the usage of the universal calendar format used by several email and calendar programs, this includes Microsoft Outlook, Apple Calendar, and Google Calendar. This in turn means that this tactic has a wide attack surface and the possibility of affecting a large number of end-users and organizations. Like all phishing usually does...

Most of us will have received bookings of meetings in our email, once the attachment is clicked a calendar event will be appended to your calendar with the descriptors specified in the file. This will often contain a link to a google or teams meeting or just an external link to some documents.
Representation:

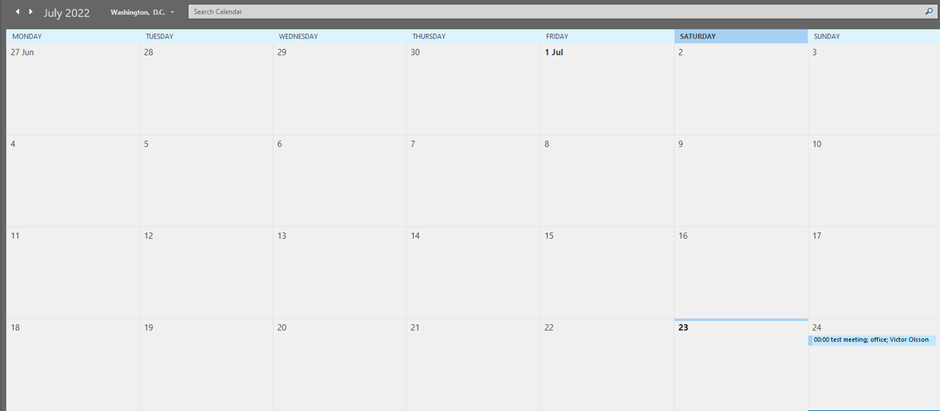
What we see is a benign booking being sent, however, with this attack, we can modify data present in the ICS file to spoof the organizer and attendees to trick a user into a false sense of security.
Calendar Spoofing
Below I will present a representation/template of what a maliciously crafted calendar booking (.ics) file can look like.
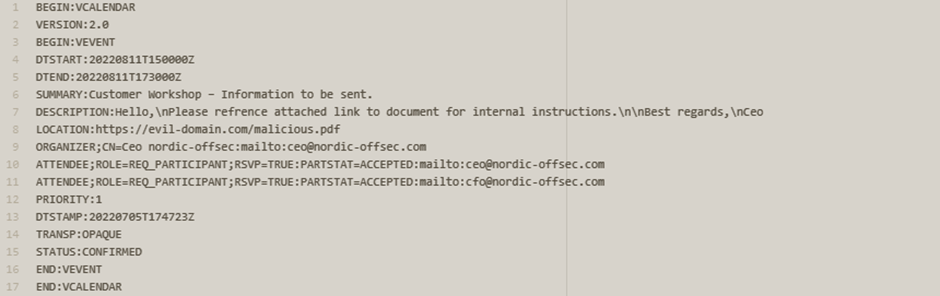
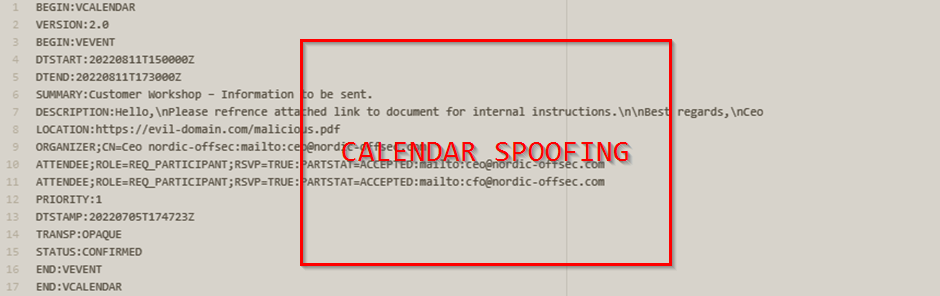
We see a clear structure of variables and values that contain data which is important to the calendar programs in order to parse the file and create an event.
For a deeper dive into the format presented you can reference:
For example, “DTSTART” & “DTEND” represents the time span of the booking, the “DESCRIPTION” will contain the body of the booking, and so on. Manipulation of the variables present in the template above could yield an efficient phishing attempt.
Using the template above, we can simply save the file as “booking.ics” and attach it to an email.
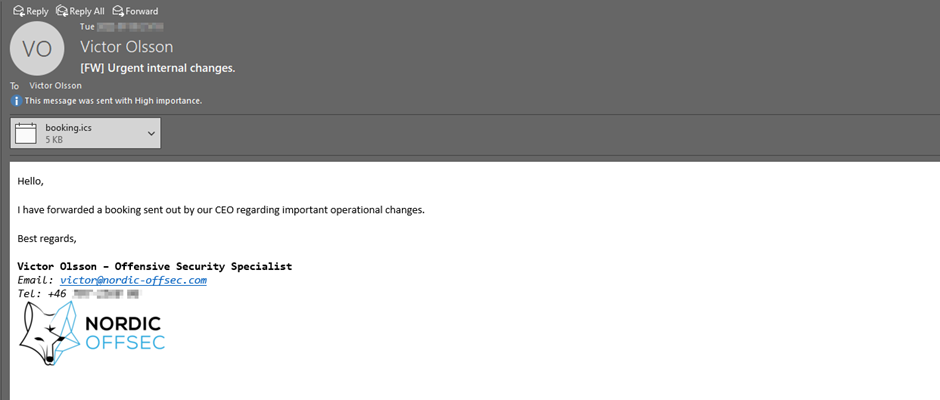
Recipient Outlook POV:
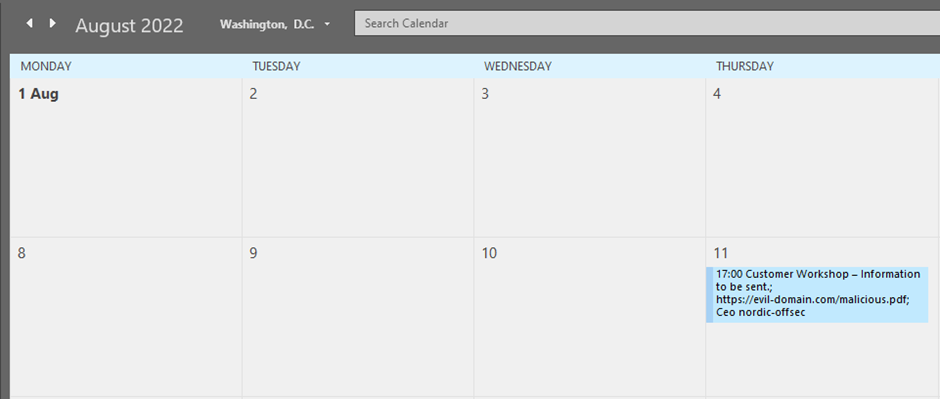
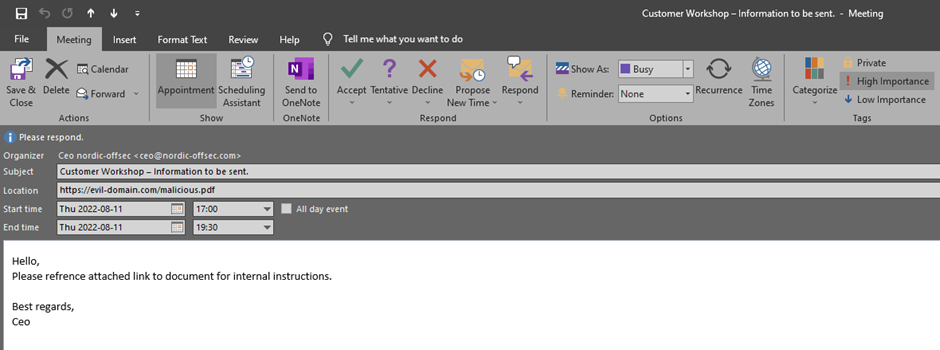
Recipient Gmail POV:
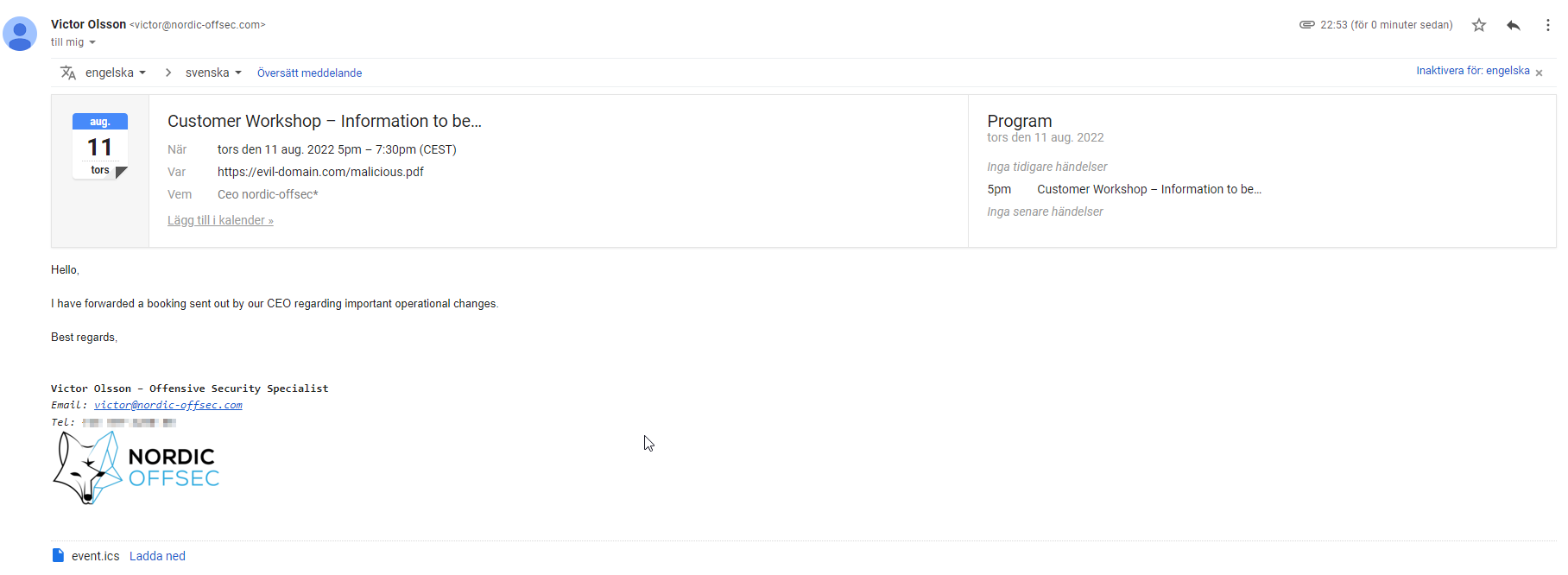
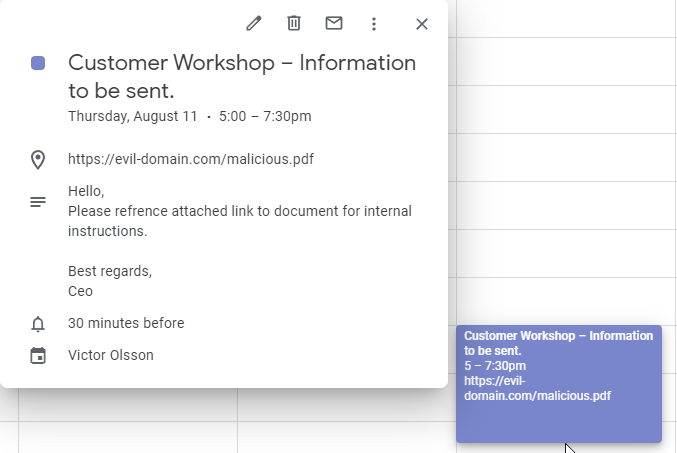
Now the booking looks more enticing and the organizer has been spoofed, making it look like the fictive CEO of Nordic Offsec has called the meeting.

Using this methodology, a threat actor or red team that has done some research (OSINT) about the target organization, can easily craft a targeted email with convincing details in order to social engineer the target to disclose information, download malware, or execute malicious instructions.
An example attack vector is to attach a link directing the user to a pdf document in the “LOCATION” value of the ICS file containing instructions to execute malicious commands.
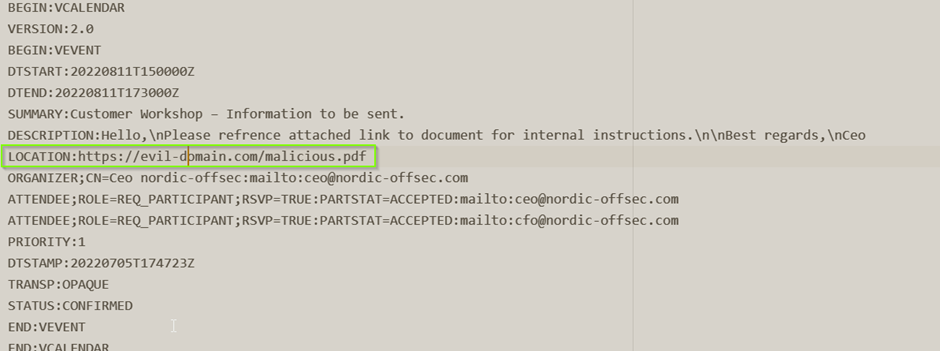
Example:
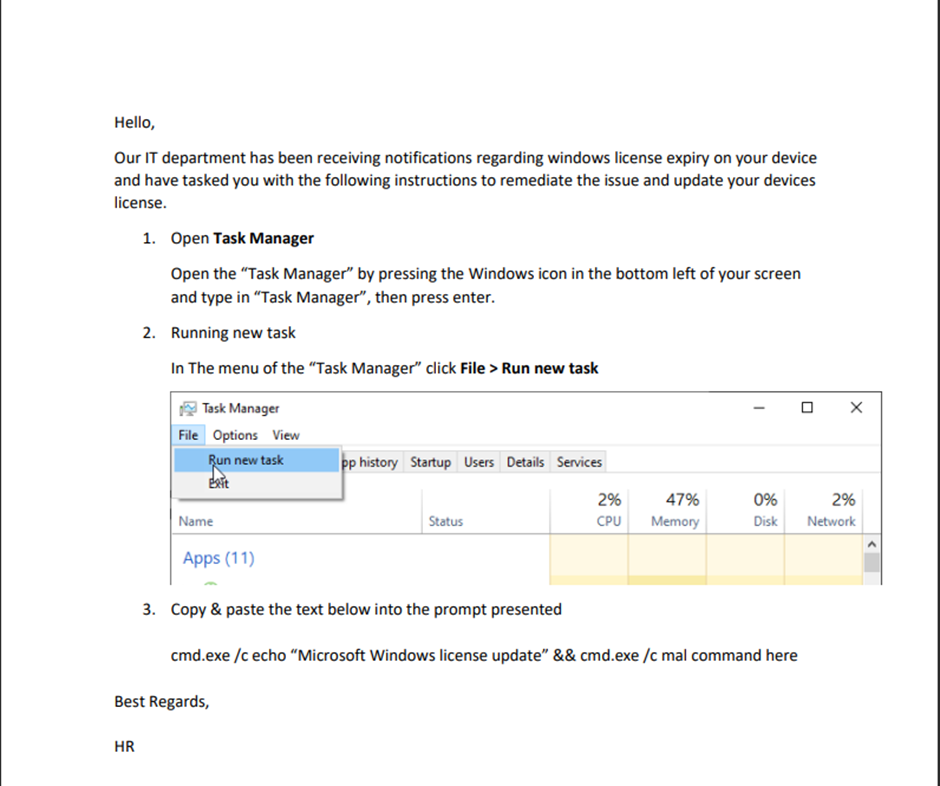
Tip!
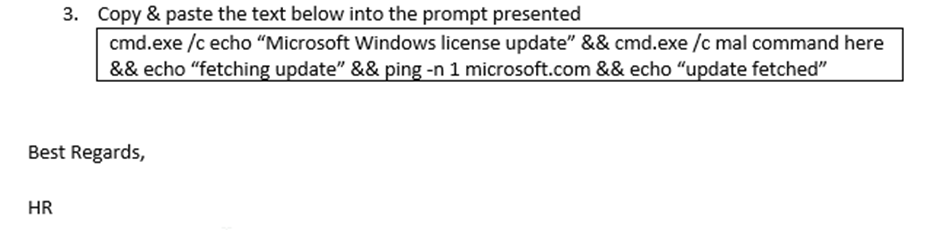
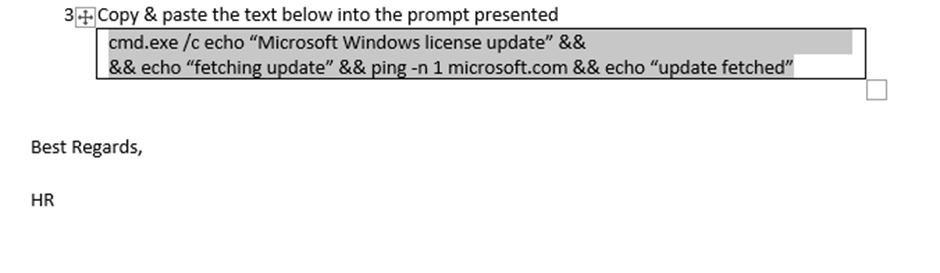
You could hide the text within the word/pdf document by changing the color of the text.
Before:
After:
As a red teamer you can of course come up with more creative ways or mimic real-world threat actors social engineering according to Threat Profiles.
This attack does not just have to be delivered by email; a threat actor could just as easily set up a website with a malicious booking which can have the same effect.
Detection & Threat Hunting
As this attack is heavily dependent on social engineering, delivery methods of malware will constantly change, meaning that detections will have to be and should be in place for a magnitude of different scenarios. defense in depths...
When looking at detection & threat hunting regarding email attack vectors it is of course important that you as a blue team first have insight into email data. Without the ability to query for data related to emails it will be harder to identify indicators of compromise for this specific attack.
If you do have the insight, looking at email attachment information such as file attachment extensions (.ics), remote URLs in combination with external senders and email context could yield some results.
Conclusion
Information shared in this blog always has the end goal of distributing information to improve security awareness.
Having a look at attack vectors that incorporate social engineering is always exciting, overall, I believe we will see more of these types of attacks in the future and hope that in some way this blog will result in some awareness distribution.
In the next blog post we will have a further look into more interesting and exciting ways threat actors attempt to obtain initial access to organizations.
Special Thanks
I initially Identified this tactic from a post created by the user @mrd0x on Twitter. And many of the aspects I go through here are presented on @mrd0x blog (https://mrd0x.com/), so thank you 😊


Member discussion